Apple Shortcuts Vulnerability Allows Easy Export of User Data
Data Privacy / Apple Security
Date: 12 March 2024
Authors:
Introduction
As reported in CVE-2024-23204 by Bitdefender security researcher Jubaer Alnazi Jabin, all Apple operating systems (i.e., macOS, iOS, iPadOS, watchOS) possessed a zero-click vulnerability in Shortcuts permitting base64 encoded messages to be transferred without explicit user consent (link). This allowed for transfer of photos and videos without acute user confirmation.
Apple responded by pushing an update to Shortcuts app requiring user confirmation in the form of a Privacy pop-up window. Note that this confirmation step requires a simple click; it does not require knowledge (i.e., “something you know”) nor biometric data (i.e., “who you are”).
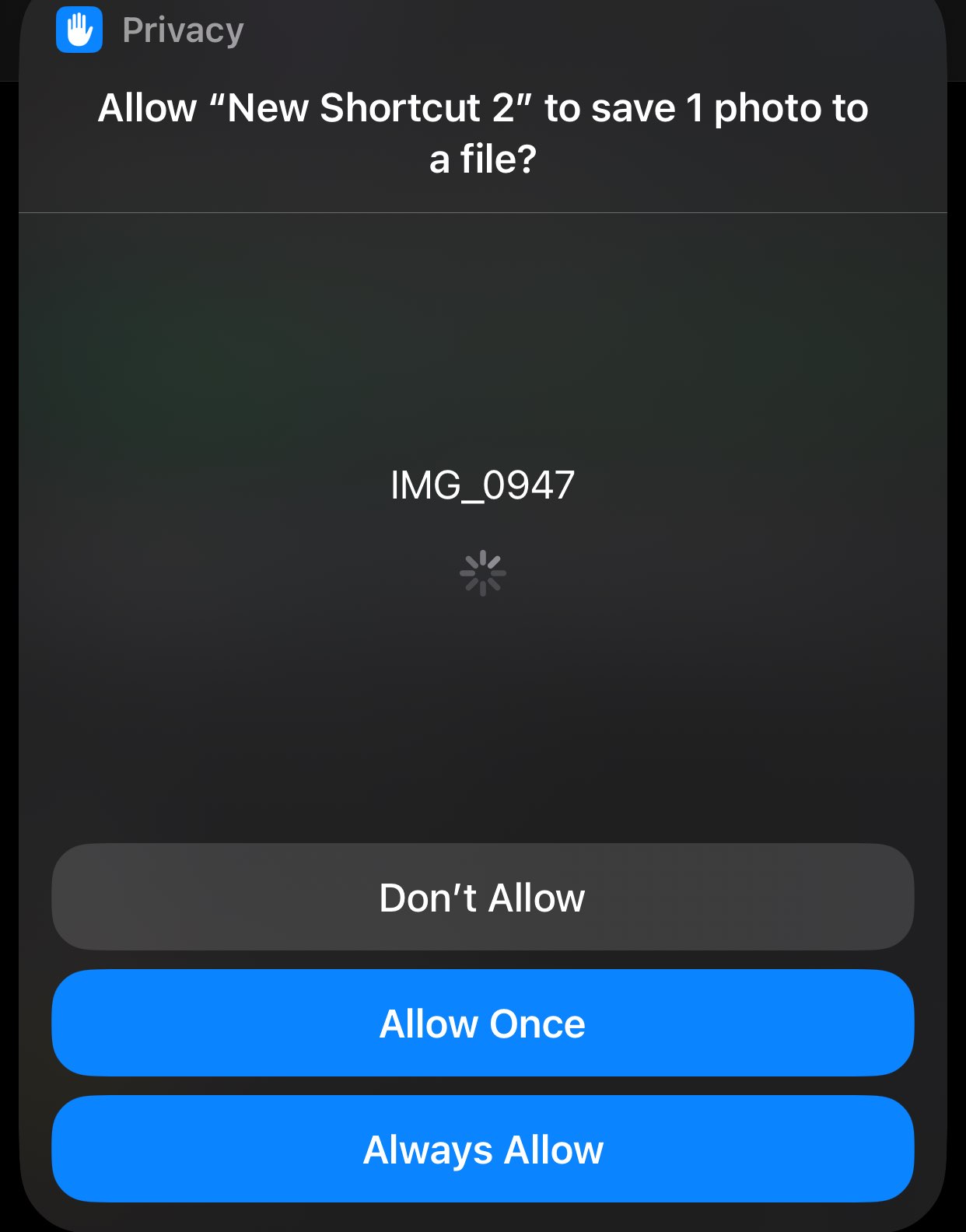
While the pop-up confirmation box is a low-level deterrent, it is insufficient in stopping attacks that leverage keylogger. Once a keylogger (or user) selects “Always Allow,” the pop-up confirmation window is satisfied, and any future attacks are performed without pop-up confirmation window.
Attack Details
Below is an example of a malicious Shortcut that easily bypasses Transparency, Consent, and Control (TCC) policies, post-vulnerability update by Apple:
| Initial Shortcut Execution with Keylogger |  |
| Remote Code Execution of Shortcuts Vulnerability with Data Exfiltration via SSH Tunneling | 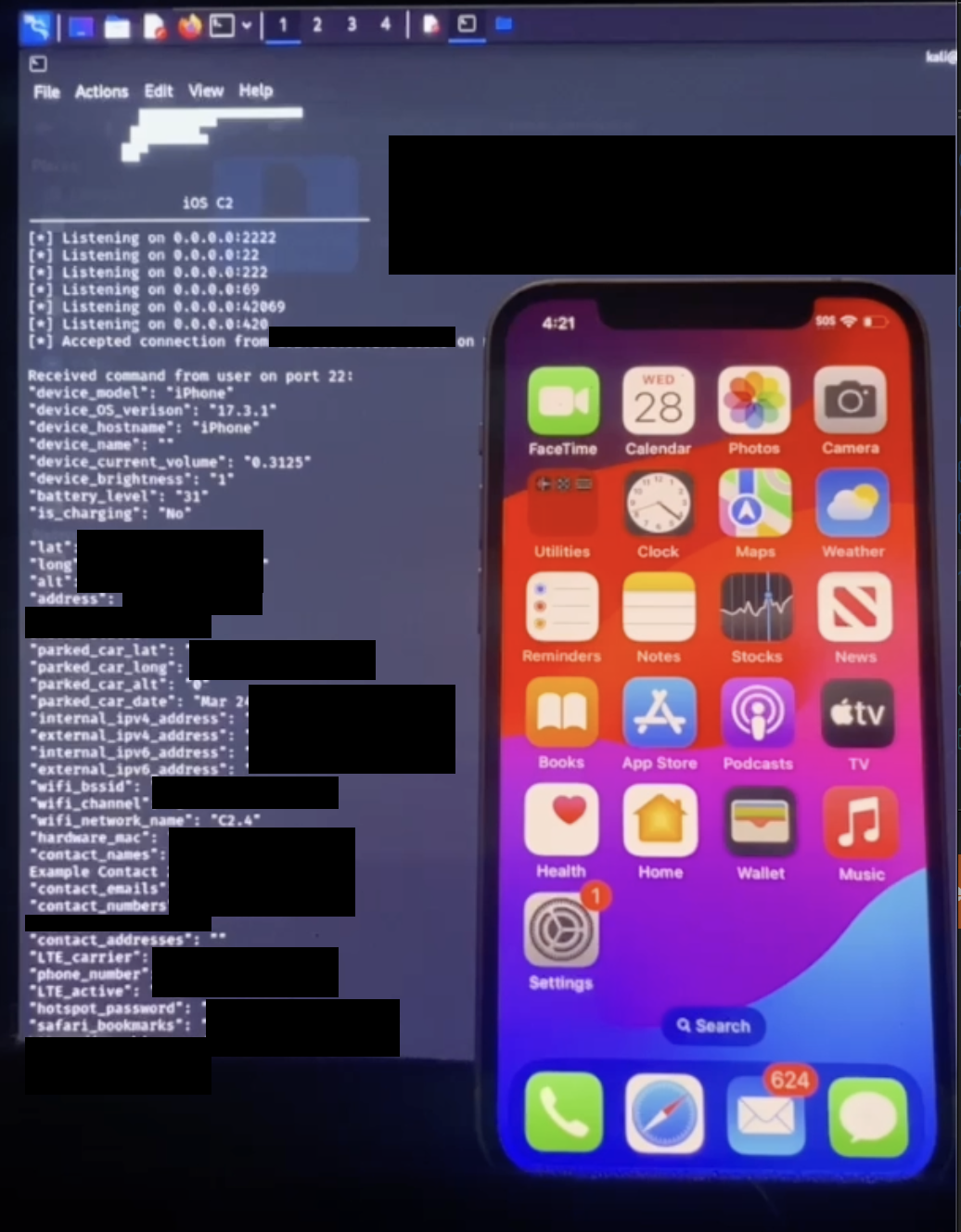 |
This is to show, the zero-click Shortcuts vulnerability is inadequately patched. The solution implemented by Apple provides nothing more than an illusion of safety. Apple users remain equally vulnerable to attack.
Beyond photos and images stored both on-device and in the Cloud, this ongoing vulnerability permits exfiltration of much more personal data:
- Contacts (e.g., Name, Phone Number, Email Address, Home Address)
- Calendar (e.g., Events and all details)
- Media (e.g., Photos, Videos, Screenshots)
- Notes
- Files
- Geolocation (e.g., GPS Coordinates, Stored Addresses, Pinned Locations)
- Network Details (e.g., Internal & External IPv4 & IPv6 Addresses, WiFi Channels, Hotspot Password)
- Hardware Details (e.g., Device Name, Hostname, System Version, MAC Address)
After submitting a detailed bug report to Apple on 24 February 2024, Apple classified this as a “non-security issue”:
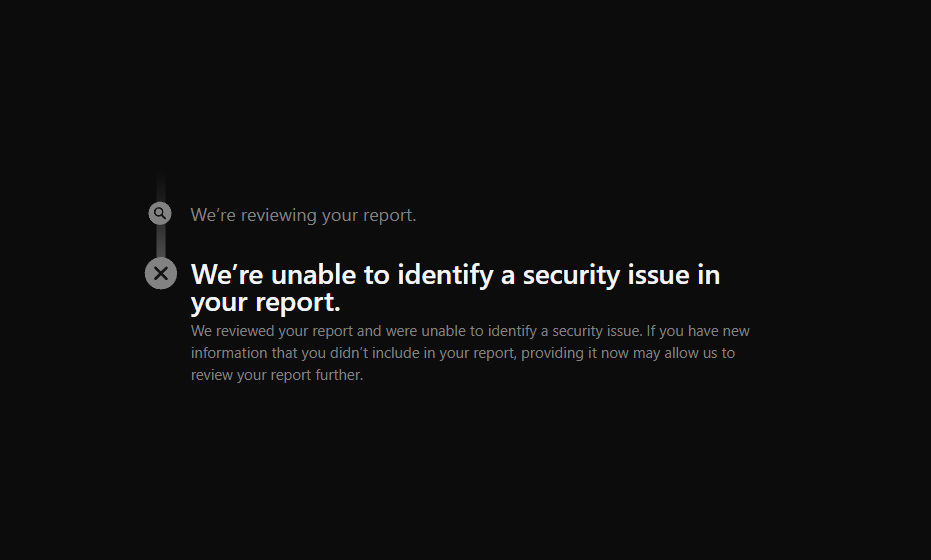
We disagree. We again push Apple to consider the following suggestions for software hardening:
- Upgrade to a password and/or biometric-based confirmation step at the time of shortcut execution.
- Upgrade Shortcuts configuration settings to include a “locked” mode requiring successful completion of two-factor authentication.
Defending
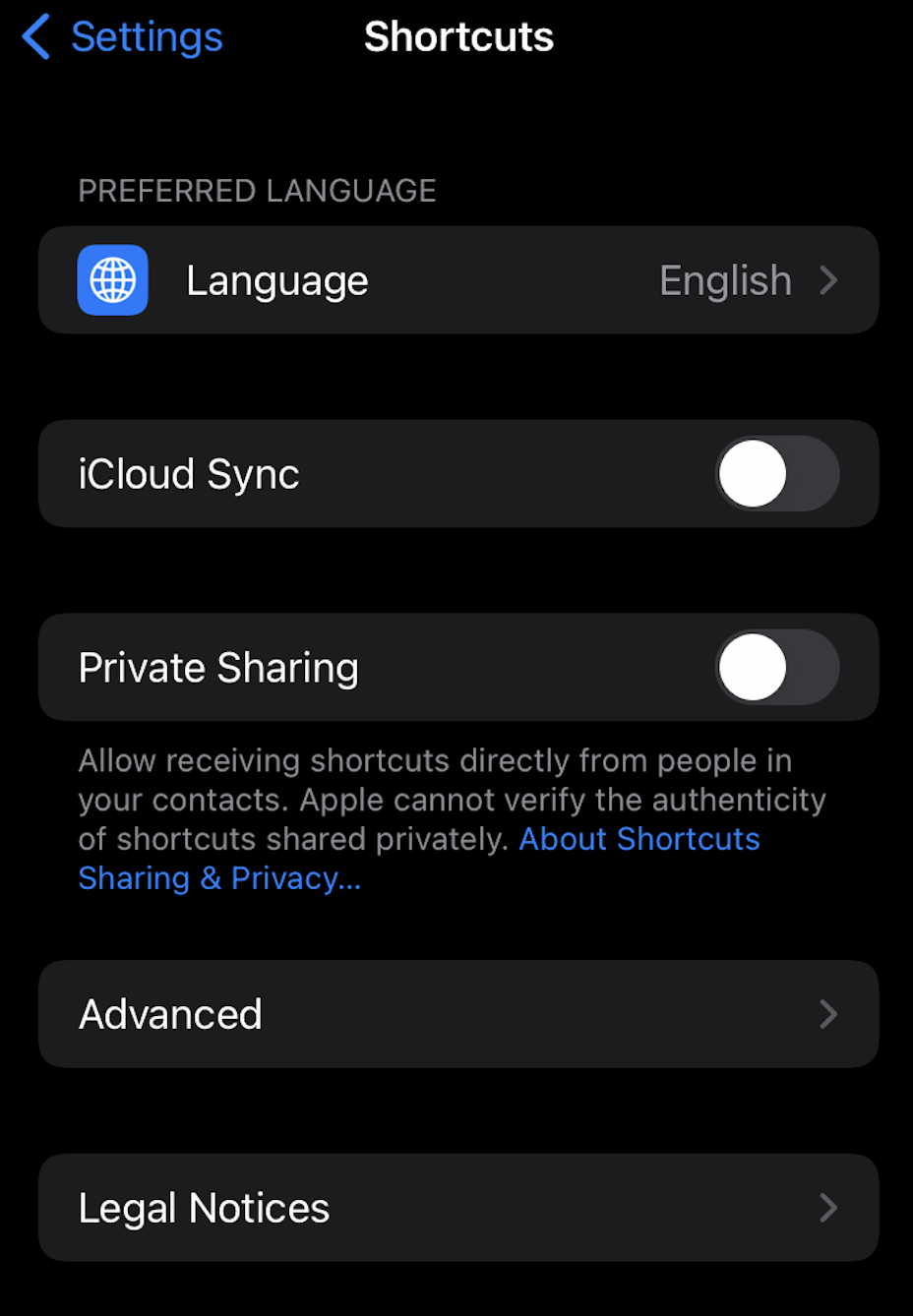
To confirm if your phone is subject to Shortcuts-based attacks, first check whether the following Shortcuts settings (Settings > Shortcuts) are “on” or “off”:
Under Shortcuts Advanced settings (Settings > Shortcuts > Advanced):
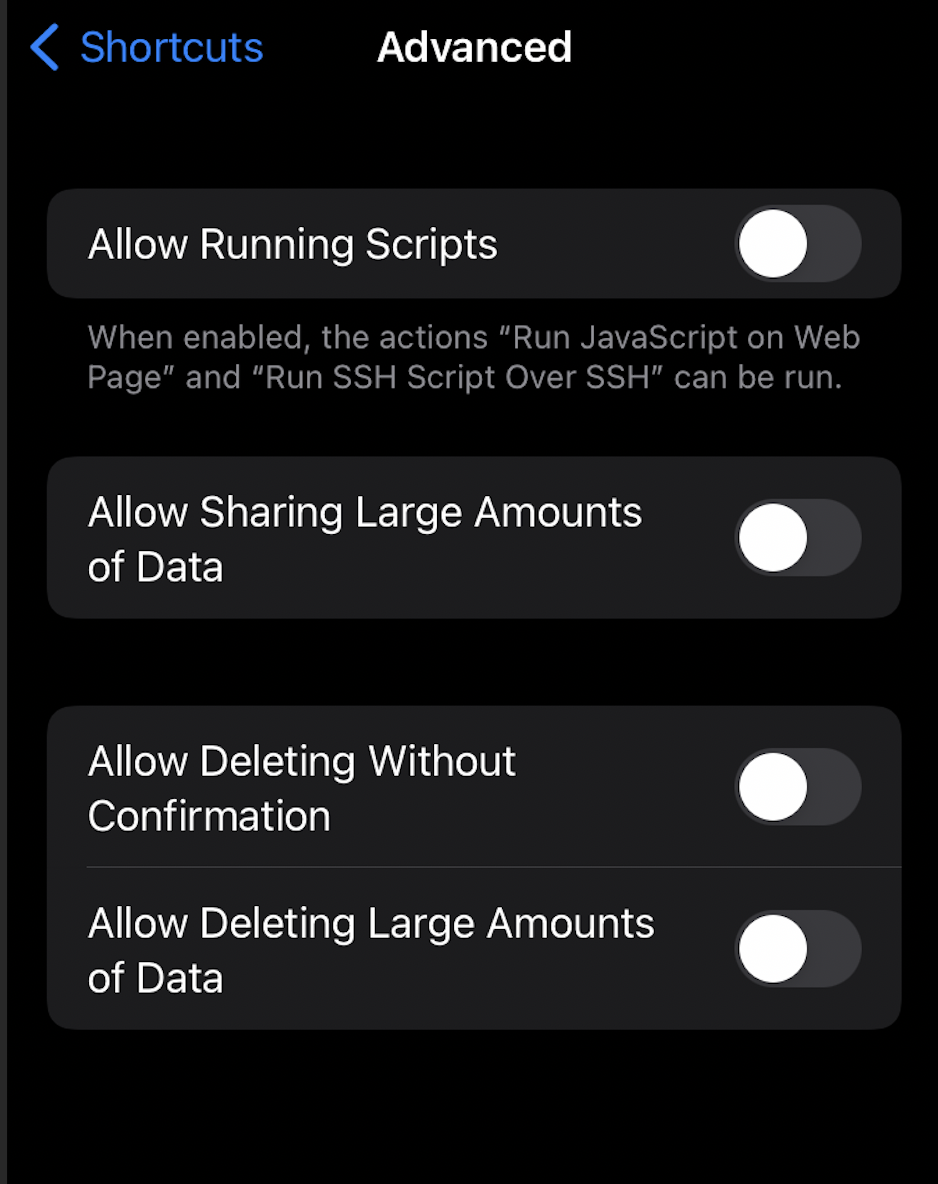
If any settings are toggled “on” (in green), consider toggling the setting off. Next, in the Shortcuts app, review the list of Shortcuts on your device, checking for the addition of any new or suspicious items.
As general precaution, we discourage persons from using charging cables you do not own or are unfamiliar with, as they could be malicious (e.g., Hak5 O.MG Cable). Additionally, because tools such as FlipperZero can execute Bluetooth-based attacks (e.g., FlipperZero iOS Bluetooth Spam Attack), we encourage persons to toggle Bluetooth “off” when not in use. We strongly suggest removing Bluetooth keyboard devices from “My Devices” list under Bluetooth Settings. Finally, we note that the Bluetooth protocol itself is especially vulnerable to attack (e.g., CVE-2023-45866). We encourage persons refrain from using Bluetooth devices as much as possible. Devices with cords are safer; embrace the cord.

